12 Ways to Prevent Cyber Crime


Simon Burge
Share this content
Cyber crime is one of the main threats of the modern age.
Understanding the nature of cyber threats is crucial for safeguarding personal and professional information and knowing ways to prevent cyber crime is vital in the modern day.
In this article, we’ll explore the intricacies of cyber crime, delve into common types, and most importantly, equip you with 12 ways to prevent cyber crime and stop you falling victim to these digital menaces.
Article Chapters
ToggleWhat is Cyber Crime?

Cyber crime is a pervasive and complex threat, encompassing a broad spectrum of illicit activities carried out online.
This multifaceted menace extends its reach across various forms of criminal behaviour, leveraging the vulnerabilities in our interconnected world.
Cyber crime manifests in diverse ways, including financial systems fraud, data breaches, identity theft, hacking, and more.
It exploits the very systems designed to facilitate communication, commerce, and connectivity.
Financial fraud, for instance, involves the manipulation of digital transactions and accounts, posing a significant challenge to individuals, businesses, and financial institutions alike.
Data breaches, another prevalent form of cybercrime, entail unauthorised access to and theft of sensitive information, ranging from personal details to corporate data.
The stolen information may be exploited for financial gain or used in other criminal activities.
As technology continues to evolve, so do the tactics employed by cybercriminals.
Their activities transcend borders, making it imperative for individuals, businesses, and governments to adopt proactive cybersecurity measures.
Understanding the nature of cybercrime is the first step towards building a resilient defence against these ever-evolving digital threats.
It requires a collective effort to mitigate risks to safeguard personal and organisational assets..
Common Types of Cyber Crime
Some of the most common forms of cyber crime include:
Ransomware

Ransomware stands as a formidable and insidious form of cyber threat, targeting individuals and organisations with malicious intent.
This type of cyber threat encrypts files on a victim’s computer or network, rendering them inaccessible.
The cybercriminal behind the attack then demands a ransom in exchange for providing the decryption key to restore access to the files.
The impact of ransomware can be devastating, leading to data loss, operational disruptions, and financial harm.
Cybercriminals often exploit vulnerabilities in software or employ social engineering tactics to infiltrate systems.
Malware
Malware, short for malicious software, constitutes a diverse category of digital threats designed to disrupt, damage, or gain unauthorised access to computer systems.
These malicious programs include viruses, worms, trojans, and spyware, each with unique functionalities.
Viruses attach themselves to legitimate programs and replicate, spreading through a system.
Worms are standalone malicious programs that replicate independently, often exploiting network vulnerabilities.
Trojans disguise themselves as benign software but unleash harmful actions once installed.
Spyware discreetly monitors and collects user information without consent.
Malware infiltrates systems through various means, including infected downloads, phishing emails, or compromised websites.
Once inside a system, it can compromise data integrity, privacy, and system functionality.
DDoS Attacks

Distributed Denial of Service (DDoS) attacks are malicious endeavours aimed at overwhelming a target’s online services or network infrastructure, rendering them temporarily or permanently inaccessible.
In a DDoS attack, a multitude of compromised devices, often part of a botnet, inundate a target with an overwhelming volume of traffic, causing a disruption in normal operations.
The goal of a DDoS attack is not to breach security or steal data but to incapacitate services by flooding them with traffic beyond their capacity to handle.
This coordinated assault can be executed through various means, such as amplification attacks and reflection attacks, exploiting vulnerabilities in network protocols.
Continuous monitoring and adaptive security strategies are essential to identifying and thwarting these disruptive assaults in the dynamic landscape of cybersecurity.
Phishing

Phishing is a deceitful cyber tactic employed by criminals to trick individuals into divulging sensitive information, such as passwords, credit card numbers, or personal details.
Typically conducted through seemingly legitimate communication channels, like emails or messages, phishing attempts often masquerade as trustworthy entities.
These deceptive messages urge recipients to click on malicious links or open infected attachments, redirecting them to fraudulent websites designed to capture confidential data.
The success of phishing lies in its social engineering approach, exploiting human psychology to create a false sense of urgency or legitimacy.
Common phishing scenarios involve impersonating reputable organisations, financial institutions, or even friends or colleagues.
12 Ways to Prevent Cyber Crime
Understanding the potential risks and adopting proactive measures are critical steps in fortifying one’s defences against the ever-growing menace of cybercrime.
Here, we delve into 12 ways to prevent cyber crime and stop yourself falling victim to these digital adversaries.
A Strong Password

The first line of defence in cyber security begins with a strong password.
Crafting complex and unique passwords that combine uppercase, lowercase, numbers, and symbols creates a formidable barrier against unauthorised access.
Regularly updating passwords and avoiding easily guessable information adds an extra layer of security, making it challenging for cybercriminals to breach accounts.
2-Factor Authentication

Enhancing login security goes beyond passwords; enabling 2-Factor Authentication (2FA) provides an additional layer of defence.
By requiring users to verify their identity through a secondary method, such as a text message or app notification, the risk of unauthorised access is significantly reduced.
Do Not Save Passwords
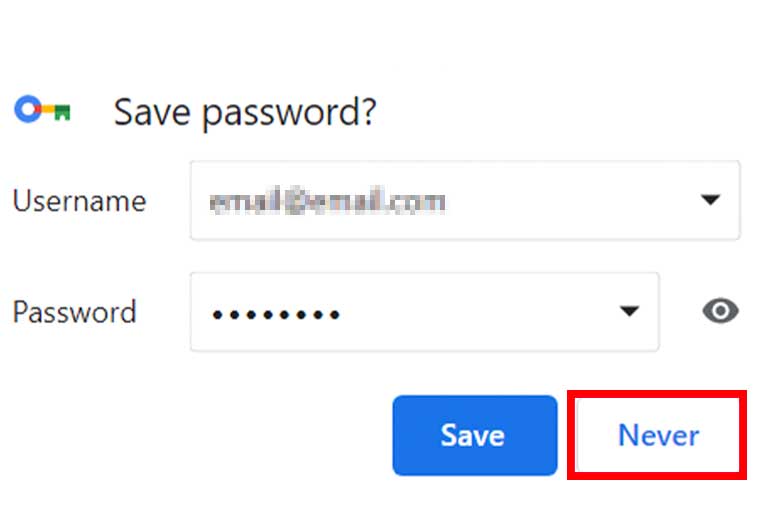
Resist the convenience of saving passwords on browsers.
Memorising them or utilising secure password managers ensures that sensitive information remains protected, reducing the risk of unauthorised access in case of a security breach.
Social Media Settings

Social media platforms are often targets for cybercriminals seeking personal information.
Reviewing and enhancing privacy settings is crucial.
Limiting the visibility of personal details minimises the potential for exploitation and protects against identity theft or other malicious activities.
Update Software
Regularly updating operating systems and software is a fundamental practice in cybersecurity.
Manufacturers continually release patches to address vulnerabilities, fortifying the defence against cyber threats.
Neglecting updates leaves systems exposed to potential exploits.
Anti-Virus Software

Investing in reputable antivirus software is a proactive measure against malware and other digital threats.
Regular scans and real-time protection capabilities can detect and neutralise potential risks before they manifest, ensuring a more secure digital environment.
Use a Firewall

A robust firewall serves as a crucial line of defence, monitoring and controlling incoming and outgoing network traffic.
By acting as a barrier against unauthorised access, firewalls play a pivotal role in safeguarding systems from potential cyber intrusions.
Never Click Spam Links

Caution is paramount when navigating the online landscape.
Clicking on suspicious links, especially in emails or on unfamiliar websites, can lead to phishing attempts or malware infiltration.
A vigilant approach reduces the risk of falling victim to these deceptive tactics.
Never Open Spam Attachments

Attachments in unsolicited emails can harbour malware capable of compromising systems.
Refraining from opening such attachments is essential in preventing potential security breaches and protecting sensitive data.
Use a VPN

Virtual Private Networks (VPNs) add an extra layer of security by encrypting internet connections.
This enhances online privacy, particularly when accessing public Wi-Fi networks.
Implementing a VPN ensures that sensitive data remains confidential and secure.
Backup Data

In the face of rising ransomware threats, regular data backups are crucial.
Storing essential information on external devices or secure cloud services safeguards against data loss in the event of a ransomware attack or hardware failure.
Educate Yourself

Knowledge is a potent weapon against cyber threats.
Staying informed about the latest developments in cybercrime and security best practices empowers individuals and organisations to adapt and fortify their defences against evolving tactics.
What to do if You Are a Victim of Cyber Crime?
Discovering that you’ve fallen victim to cybercrime can be distressing, but a swift and strategic response can mitigate further damage. If you suspect you are a victim:
Isolate the Compromised System

Disconnect the affected device from the internet to prevent further unauthorised access and to contain the potential damage.
Change Passwords

Immediately change passwords for compromised accounts.
Choose strong, unique passwords to enhance security.
Scan for Malware
Conduct a thorough antivirus scan on the affected device to identify and eliminate any malware that may have contributed to the breach.
Report to Authorities

File a report with relevant law enforcement agencies, providing details of the incident.
This aids in potential investigations and helps authorities track and apprehend cybercriminals.
Contact Your Bank

If financial information is compromised, notify your bank and credit card companies promptly.
They can take preventive measures and help you monitor for any suspicious activities.
Inform Relevant Parties

If the incident involves personal or sensitive data of others, inform the affected parties promptly and transparently, as this fosters trust and enables them to take necessary precautions.
Seek Professional Help

Engage with cybersecurity professionals to assess the extent of the breach, recover lost data, and fortify your digital defences against future attacks.
Learn and Prevent

Understand the method of attack and learn from the experience.
Implement additional security measures, such as two-factor authentication and regular data backups, to fortify your online presence.
Monitor Your Accounts

Continuously monitor your accounts for any unusual activities.
Regularly check credit reports to ensure no unauthorised accounts or transactions have occurred.
The Future of Preventing Cyber Crime

The future of preventing cyber crime is poised to be both challenging and innovative as technology evolves and cyber criminal tactics become more sophisticated.
Artificial Intelligence (AI) and machine learning will play pivotal roles in fortifying cybersecurity.
These technologies can analyse vast amounts of data in real-time, identifying patterns and anomalies that may indicate potential threats.
Blockchain technology is also emerging as a disruptor in the field.
Its decentralised and transparent nature can enhance the security of digital transactions, making it harder for cybercriminals to manipulate or exploit financial systems.
Collaboration between governments, private sectors, and individuals will become increasingly crucial.
Sharing threat intelligence and best practices can create a united front against cyber threats, fostering a collective defence against evolving tactics.
Moreover, as our lives become more interconnected through the Internet of Things (IoT), securing these devices will become paramount.
Implementing robust security measures in smart homes, connected vehicles, and industrial IoT systems will be essential to prevent cyber intrusions.
Cybersecurity training will be integrated into educational curricula and professional development programs, empowering individuals to recognize and thwart potential threats in their digital interactions.
As the digital landscape evolves, a proactive and collaborative approach will be key to staying ahead of cybercriminals and ensuring a secure digital future.
Conclusion
You should now have more of an understanding of the digital dangers you can face and ways to prevent cyber crime.
Securing oneself in the digital age requires a proactive approach.
By understanding the nature of cyber threats and implementing these 12 ways to prevent cyber crime, individuals and organisations can fortify their defence.

