What is Endpoint Application Isolation & Containment Technology?

Simon Burge
Share this content
Endpoint application isolation and containment technology is a cybersecurity solution which aims to protect computer systems by isolating and containing malicious applications from executing potentially harmful actions.
The technology creates a secure environment in which potentially dangerous applications are executed, preventing them from accessing other parts of the system and potentially causing harm.
Endpoint application isolation and containment technology is becoming increasingly important as the number of cyber attacks targeting businesses and individuals continues to rise.
By isolating and containing suspicious applications, this technology can help to prevent malware infections, data breaches, and other security incidents.
In the following chapters, we outline why endpoint application isolation is important in modern networks, the benefits of endpoint application isolation and when businesses reliant on computers, servers and connected technology need to consider implementing containment procedures.
Article Chapters
ToggleWhen is Endpoint Application Isolation Needed?
Endpoint application isolation would be required in situations where there’s a genuine risk of malware infection or other cyber threats.
It can be used to protect individual endpoints such as desktops, laptops, and mobile devices, as well as servers and virtual machines.
This technology is particularly useful in environments where sensitive data is stored or where there is a high risk of cyber attacks, such as financial institutions, healthcare organisations, and government agencies.
Endpoint application isolation can also be used to protect remote workers or contractors who may be accessing corporate resources from unsecured networks or devices.
By isolating and containing potentially malicious applications, this technology can help to prevent the spread of malware and limit the impact of cyber attacks.
What Happens During Endpoint Application Isolation & Containment?
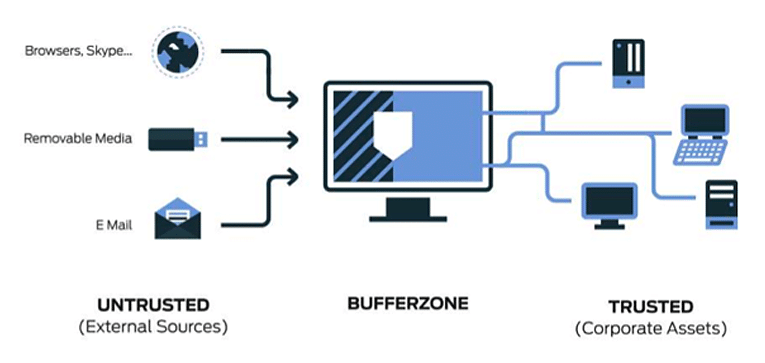
In the event of a malware-induced breach, the endpoint affected would be identified by the cybersecurity solution and isolated to prevent further damage.
This containment measure would effectively stop it in its tracks, and terminate all network access on the compromised endpoint.
During endpoint application isolation, potentially malicious applications are executed in a contained environment or sandbox that is isolated from the rest of the system.
This means that the application is prevented from accessing other parts of the system or making changes to critical files or settings.
The isolated environment is often designed to mimic the real operating system, but with additional security measures in place, such as restrictions on network access, file system access, and system calls.
Once the application is isolated, it can be analysed to determine if it is indeed malicious or otherwise.
This is typically done using behavioral analysis or other techniques that can detect suspicious activity.
If the application is found to be malicious, it can be quarantined or removed from the system before it can cause further damage.
Endpoint application isolation can also be used to protect against zero-day exploits and other unknown threats.
By isolating applications and preventing them from interacting with other parts of the system, even previously unknown threats can be contained and prevented from spreading to other endpoints or compromising critical data.
What are the Different Modes of Endpoint Isolation?
There are several different modes of endpoint isolation that can be used depending on the specific security requirements and use case.
Here’s some common modes of endpoint isolation:
Full System Isolation
The entire system is isolated from the network and other endpoints.
This can be used to protect critical systems or in high-security environments where there is a risk of malware infections or cyber attacks.
Process Isolation
This technique manages the processes that are permitted to initiate, run, and continually function on the endpoint.
Application Isolation
Only specific applications are isolated and executed in a secure sandbox environment.
This can be used to protect against malware infections or to test new or potentially risky applications before they are deployed in the production environment.
Desktop Isolation
Notifies the end-user and promptly ceases any additional activity to minimise harm.
The system remains online, but access is restricted to the Malwarebytes cloud console.
Containerisation
Containerisation is a type of application isolation that uses container technology to create a secure and isolated environment for applications to run in.
This can be used to protect applications and data from other applications running on the same system.
Network Isolation
The endpoint is isolated from the network and can only communicate with specific servers or endpoints.
This can be used to prevent malware infections from spreading to other parts of the network.
Virtualisation
This technology allows multiple virtual machines to run on a single physical machine.
Each virtual machine is isolated from the others and can run its own operating system and applications.
This can be used to provide secure and isolated environments for different applications or to test new software configurations.
Why Use Application Isolation?
Vendors and their clients are increasingly adopting application isolation as a means to address the issues discussed above.
This approach aligns with the fundamental principles of zero trust, including least privilege, robust identity, and mandatory access controls.
Isolation is a crucial component of zero trust, and it is often accomplished through network micro-segmentation to limit lateral movement.
However, the same concept can be applied to applications and data within an endpoint by utilizing hypervisor-level virtualization.
Benefits of Application Isolation

Application isolation offers several benefits for organisations seeking to enhance their endpoint security.
Some of these benefits include:
Reduced Risk of Malware Infections
Application isolation can help to prevent malware from infecting other parts of the system by containing potentially malicious applications in a secure sandbox environment.
Improved Security Posture
By isolating applications, organisations can implement a zero-trust security approach that limits access to critical resources and data.
This can help to reduce the risk of cyber attacks and data breaches.
Increased Flexibility
Application isolation can enable organisations to run different applications on the same system without worrying about compatibility issues or security risks.
This can improve productivity and enable organisations to adopt new applications or technologies more quickly.
Easier Management
Application isolation can simplify endpoint management by allowing IT teams to manage and update applications in a centralised environment.
This can reduce the workload of IT staff and improve overall efficiency.
Reduced Downtime
In the event of a security incident, application isolation can limit the impact and reduce downtime by containing the threat and preventing it from spreading to other parts of the system.
Reduced Operational Costs
Minimises expenses relating to the aftermath of security breaches and the procurement of dedicated laptops solely for accessing sensitive corporate assets.
Provides Insights
Offers invaluable insights for threat hunter teams and incident responders, empowering them to mitigate risks more effectively and improve their resilience to potential future attacks.


