What is Industrial Control Systems Security?


Simon Burge
Share this content
The term Industrial Control Systems (ICS) refers to a diverse range of controls and instrumentation used for operating and automating industrial processes.
This included a broad spectrum of equipment, systems, networks, and controls.
Every industry has its own unique way of using industrial control systems to manage tasks electronically.
These systems are essentially designed to make things run smoothly and more efficiently.
Nowadays, the devices and protocols used in ICS are found in almost every business sector, including manufacturing, transportation, energy, and water treatment.
They play a crucial role in these industries’ operations and infrastructure.
However, the use of smart devices and the Internet of Things (IoT) is changing the way Industrial control systems (ICS) work.
Whilst this makes things easier, faster and more productive in ICS environments, it also raises the genuine concern about how secure ICS systems really are.
In this article, we take a closer look at what industrial control systems are and how they’re used.
This includes the different types of ICS systems available, their key components, plus common threats and challenges they face, and best practices to mitigate risks.
Article Chapters
ToggleWhat are Industrial Control Systems (ICS)?
Industrial security systems refer to digital device assets used in industrial processes.
These assets are used in various sectors, including critical infrastructure like the power grid, water treatment facilities, and transportation systems.
They’re also instrumental in manufacturing plants and similar applications where efficient control and automation are essential.
Within the realm of critical infrastructure, ICS assets enable the smooth operation and management of essential services.
For instance, in the power grid, these assets include devices responsible for monitoring electricity generation, distribution, and transmission.
They ensure that power is reliably delivered to homes, businesses, and public facilities.
Similarly, in water treatment facilities, ICS assets are employed to regulate the purification, filtration, and distribution of clean water, ensuring a safe and uninterrupted supply.
In manufacturing, ICS assets are integral to optimising production processes.
They work together to automate tasks, monitor production lines, control machinery, and maintain quality standards.
Industrial control system assets in manufacturing environments enable streamlined operations, increased efficiency, and improved productivity.
The versatility of ICS assets is not limited to critical infrastructure and manufacturing alone.
They find application in a diverse range of sectors, including oil and gas refineries, chemical plants, transportation systems, and more.
In each of these domains, ICS assets contribute to enhanced control, improved safety measures, optimised resource allocation, and better overall performance.
As technology advances, the capabilities of ICS assets continue to evolve.
Integration with modern communication networks, cloud-based solutions, and advanced analytics enables more efficient data collection, analysis, and decision-making.
However, it’s important to ensure that the security of ICS assets is maintained, as any vulnerabilities or unauthorised access to these devices can have significant consequences for industrial operations and critical infrastructure.
Types of Industrial Control Systems
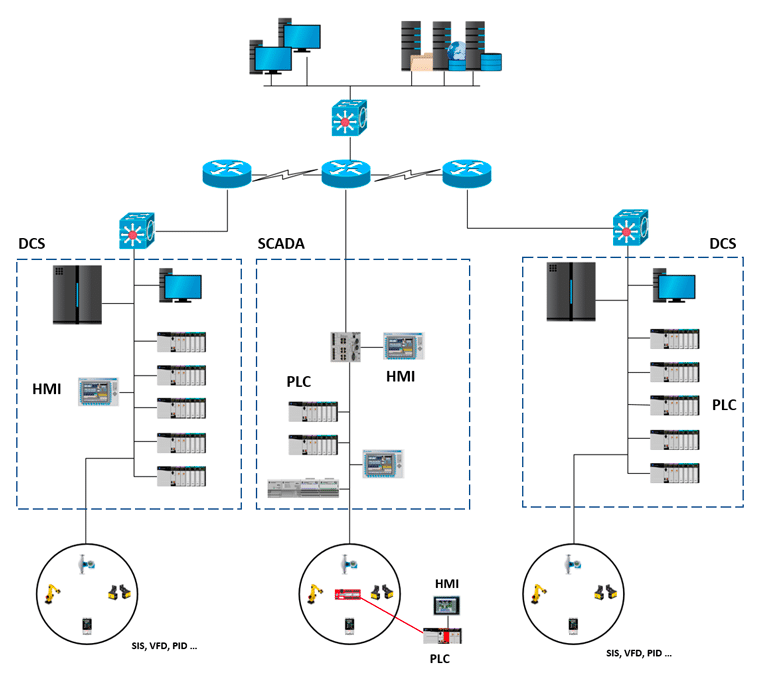
There’s a number of different types of industrial control systems, with the two most notable examples being Supervisory Control and Data Acquisition (SCADA) systems, and Distributed Control Systems (DCS).
Local operations are controlled by Field Devices, which receive commands from remote stations.
Here’s a more in-depth breakdown of the main types of ICS’s:
Supervisory Control and Data Acquisition (SCADA)
Industries that rely on SCADA systems include those involved in pipeline monitoring and control, water treatment centers and distribution, and electrical power transmission and distribution
SCADA systems offer supervisory control rather than full control.
These systems consist of devices, typically Programmable Logic Controllers (PLCs) or other commercial hardware modules, distributed across different locations.
SCADA systems are capable of receiving and transmitting data.
They are integrated with a Human Machine Interface (HMI) that enables centralised monitoring and control of various process inputs and outputs.
SCADA systems serve the main purpose of remotely monitoring and controlling field sites from a centralized control system.
Instead of requiring manual travel to perform tasks or collect data, SCADA automates these processes.
Field devices within the system are responsible for controlling local operations, such as managing valve and breaker operations, collecting data from sensor systems, and monitoring the local environment for alarm conditions.
Distributed Control System (DCS)
DCS systems have widespread use in various industries including manufacturing, electric power generation, chemical manufacturing, oil refineries, and water and wastewater treatment.
A DCS is a control system specifically designed for managing production systems within a single location.
In a DCS, a setpoint is transmitted to the controller, which then instructs valves or actuators to operate in a manner that maintains the desired setpoint.
Field data can be stored for future reference, used for basic process control, or utilised in advanced control strategies involving data from other areas of the plant.
A DCS employs a centralized supervisory control loop to oversee and manage multiple local controllers or devices within the production process.
This enables industries to swiftly access production and operation data.
Moreover, by utilising multiple devices throughout the production process, a DCS can minimise the impact of a single fault on the entire system.
Actual ICS implementation
When implementing an ICS (Industrial Control System) environment, it’s common to have a hybrid approach that combines attributes from both DCS (Distributed Control System) and SCADA (Supervisory Control and Data Acquisition) systems.
This allows for the incorporation of features and functionalities from both systems to meet specific operational needs.
Key ICS Components
ICS has a long history, and while they have been connected in networks for many years, they were typically kept isolated from the Internet through an “air gap.”
This measure was taken to enhance their protection against cyber threats by making it harder for unauthorized remote access and exploitation.
More recently, the concept of the air gap has diminished.
Nowadays, it’s common to utilise Internet-connected smart and IoT devices for remote monitoring and management of ICS.
While this brings about improved efficiency and usability, it also introduces new cybersecurity threats.
This shift necessitates the implementation of ICS and IoT security solutions to safeguard the safety and functionality of these newly Internet-connected systems.
Information Technology (IT) & Operational Technology (OT)
Operational Technology (OT) encompasses the hardware and software systems responsible for monitoring and controlling physical devices in various fields.
The specific tasks performed by OT can vary depending on the industry.
For instance, devices used to monitor temperature in industrial environments are examples of OT devices.
These devices play a crucial role in maintaining optimal conditions and ensuring the smooth operation of industrial processes.
Programmable Logic Controller (PLC)
This hardware component is utilised in both DCS and SCADA systems to serve as a control element within the overall system.
It plays a key role in locally managing processes by utilizing feedback control devices like sensors and actuators.
Within the context of SCADA, PLCs (Programmable Logic Controllers) perform a similar role to Remote Terminal Units (RTUs).
In DCS, PLCs are employed as local controllers within a supervisory control framework.
Additionally, PLCs are commonly used as primary components in smaller control system configurations.
Remote Terminal Unit (RTU)
An RTU, which stands for Remote Terminal Unit, is a field device equipped with a microprocessor that performs control, and data management and acquisition functions.
Its main purpose is to receive commands from a Master Terminal Unit (MTU) and transmit relevant information back to the MTU.
The RTU serves as an intermediary between the MTU and various field devices, such as sensors, actuators, and other equipment deployed in remote locations.
It collects data from these devices, including measurements, status updates, and alarms, and sends this information to the MTU for further processing and analysis.
Control Loop
In a control loop, hardware components like PLCs and actuators are utilised.
The control loop interprets signals from sensors, control valves, breakers, switches, motors, and similar devices.
The measured variables from these sensors are then transmitted to the controller, which performs tasks and/or completes processes based on the received signals.
Human Machine Interface (HMI)
A graphical user interface (GUI) application serves as an interface between the human operator and the controller hardware in an ICS environment.
It enables interaction, displays status information, and presents historical data collected by devices.
The GUI is essential for monitoring and configuring setpoints, controlling algorithms, and adjusting parameters in the controllers.
Control Server
A control server is responsible for hosting the supervisory control software of a DCS or PLC.
It serves as a communication hub, connecting and exchanging data with lower-level control devices.
Master Terminal Unit (MTU)
A Master Terminal Unit (MTU) is a central device in a control system that serves as the main controller or supervisory unit.
It’s responsible for gathering and processing data from remote field devices, such as RTUs (Remote Terminal Units) or PLCs (Programmable Logic Controllers), and issuing commands to control and monitor industrial processes.
The MTU acts as the central point of coordination and decision-making in the control system.
It receives and analyses data from field devices, and based on predetermined algorithms or control strategies, generates control signals or instructions to adjust parameters, activate or deactivate functions, and ensure the smooth operation of the controlled processes.
Intelligent Electronic Device (IED)
An Intelligent Electronic Device (IED) is a smart device that can acquire data, communicate with other devices, and perform local processing and control functions.
The integration of IEDs into control systems such as SCADA and DCS enables automated control at the local level.
These devices play a crucial role in efficiently and autonomously managing various processes within the control system.
Data Historian
A data historian serves as a centralised database within an ICS environment, recording and storing all process information.
It facilitates the export of data to the corporate Information System (IS).
The gathered data is utilised for process analysis, statistical process control, and enterprise-level planning purposes.
Remote Diagnostics
Remote diagnostics refers to the process of identifying, preventing, and recovering from abnormal operations or failures in a system or equipment without the need for physical presence at the location.
It involves utilising technology and remote access capabilities to diagnose, monitor, and resolve issues.
Typical Threats to Industrial Control System (ICS)?

Attacks targeting Industrial Control Systems (ICS) devices can result in intentional or unintentional disruptions, leading to a loss of availability.
There are several ways in which attackers can gain unauthorized access to these systems, including:
Lateral Movement from IT Network
Once inside the IT network, attackers can attempt to pivot and move laterally into the ICS environment, taking advantage of interconnected systems and weak security controls.
Direct Access to Internet-Facing Systems
If ICS devices are directly accessible from the internet, attackers can exploit vulnerabilities or weak authentication mechanisms to gain entry and compromise the system.
Phishing Attacks
Attackers may employ phishing techniques to trick employees into revealing their credentials, providing the attackers with legitimate access to the ICS environment.
Exploit Vulnerable Connected Systems
IoT devices and other internet-connected systems present potential entry points for attackers.
If these devices are not properly secured or have known vulnerabilities, they can be exploited to gain unauthorised access to the ICS infrastructure.
To enhance system functionality and productivity, Industrial Control Systems (ICS) continually integrate new technologies and software in both IT and OT domains.
However, the convergence of IT and OT also amplifies their attractiveness as targets for cybercriminals.
One significant security challenge lies in safeguarding legacy control systems like SCADA, where many security solutions exhibit vulnerabilities.
Moreover, organisations must confront the emergence of security threats associated with modern technologies such as cloud computing, big data analytics, and the Internet of Things (IoT).
The centralisation of systems introduces unfamiliar vulnerabilities into the cyber ecosystem, necessitating robust security measures to mitigate potential risks.
Attacks on Industrial Control Systems (ICS) typically involve targeted strategies that exploit the entry point of the ICS to establish a presence within a system.
This foothold enables lateral movement through the organisation.
Notable examples of such attacks include the Stuxnet worm, which manipulated centrifuges in Iranian nuclear facilities, and BlackEnergy malware, which impacted power generation facilities in Ukraine.
While many attacks primarily aim for data theft or industrial espionage, these prominent cases demonstrated that malware can have physical consequences, known as a kinetic effect.
In these instances, the malware directly influenced the operation of critical infrastructure, showcasing the potential for significant disruption and damage.
Industrial Control Systems Security Best Practices
To enhance the security of Industrial Control Systems (ICS), it’s essential to bridge the gap that often exists between the level of protection in ICS systems compared to IT systems.
Implementing the following best practices can help improve ICS system security:
ICS Asset Discovery
This is crucial to enhancing industrial security management.
It involves gaining a comprehensive understanding of the complete ICS infrastructure and its network connectivity.
This process helps organisations identify all ICS assets within their systems, including devices, controllers, and network components.
By obtaining full visibility into the ICS assets, organisations can effectively manage and secure their infrastructure, ensuring that appropriate security measures are in place to protect against potential threats and vulnerabilities.
Monitor Networks
Monitoring ICS networks is essential as these networks typically exhibit a static nature, with infrequent changes in connected devices.
To enhance security, it’s crucial to establish a baseline for normal network behavior through continuous monitoring.
This involves monitoring network traffic and device activities to identify any anomalies or deviations from the established baseline.
Additionally, the monitoring process should be capable of detecting and providing alerts for any new devices that connect to the network.
By actively monitoring ICS networks, organisations can promptly identify and respond to any potential security threats or unauthorised changes, ensuring the integrity and stability of the network environment.
Network Segmentation
In the past, ICS networks were safeguarded through air gaps, but this approach is no longer sufficient.
Ensuring the security of systems that were not initially designed for internet connectivity now demands network segmentation.
This involves implementing firewalls that possess a deep understanding of ICS protocols, effectively isolating and protecting the various components within the network.
By adopting this strategy, organisations can enhance the security of their ICS infrastructure, mitigating the risks associated with internet connectivity while maintaining operational efficiency.
Least Privilege
Numerous ICS protocols lack proper access controls, which can lead to unauthorised access to critical and potentially hazardous functionalities.
To address this vulnerability, it’s crucial to employ ICS protocol-aware firewalls.
These firewalls are specifically designed to enforce access controls on ICS network traffic, ensuring that only authorised entities can interact with sensitive functions.
By implementing such firewalls, organisations can bolster the security of their ICS systems, safeguarding them against unauthorised access and potential malicious activities.
Intrusion Prevention Systems (IPS)
Relying solely on detection-focused ICS security leaves organisations in a reactive stance, responding to existing malware infections and security incidents.
To proactively protect ICS systems, it’s crucial to implement an Intrusion Prevention System (IPS).
The IPS plays a critical role in identifying and blocking attempted exploitations of known vulnerabilities in both ICS systems and the legacy operating systems they utilise.
By implementing an IPS, organisations can strengthen their security, preventing potential attacks and minimising the risk of successful exploitation, ultimately ensuring the stability and integrity of their ICS infrastructure.
Secure Remote Access
Remote access is frequently required to monitor and manage geographically dispersed ICS assets.
However, it’s vital to ensure that this access is established with robust authentication, access control, and encryption measures in place.
These security measures are essential for safeguarding against unauthorised access to and exploitation of the systems.
By implementing strong authentication protocols, strict access controls, and robust encryption mechanisms, organisations can significantly reduce the risk of unauthorised individuals gaining access to critical ICS assets and protect the integrity and confidentiality of their systems.
Secure Physical Access
Physical access to ICS assets poses a significant threat to their availability and can potentially bypass cybersecurity defenses.
To ensure comprehensive protection, it’s essential to implement a combination of both cyber and physical security measures for ICS environments.
Cybersecurity measures safeguard against unauthorised access and attacks from digital sources, while physical security measures aim to restrict physical access to ICS assets.
By integrating robust cyber and physical security measures, organisations can enhance the overall protection of their ICS assets, mitigating the risk of disruptions, unauthorised tampering, and compromise of critical systems.
Conclusion
Industrial control systems (ICS) play a critical role in maintaining the functionality of essential infrastructure, manufacturing processes, and related industries.
However, their complexity and vulnerability make them susceptible to various types of attacks.
To ensure the security and integrity of ICS environments without disrupting normal operations, the implementation of ICS-aware security measures becomes imperative.
These security measures are specifically designed to address the unique challenges and risks associated with ICS, providing the necessary protection to safeguard against potential attacks while maintaining uninterrupted system operations.
By embracing ICS-aware security solutions, organisations can effectively protect their critical infrastructure and industrial processes, ensuring the reliability, safety, and continuity of their operations.



