ISJ Exclusive: Why the cloud is the preferred architecture for mission critical systems

James Thorpe
Share this content
Besides the more modern, flexible architecture and ability to control and monitor your system from anywhere, the most compelling reason to make the move to the cloud is the rapid escalation of ransomware attacks hitting businesses – particularly small businesses, reports Keri Systems.
There is a better than one in three chance that your business will be the target of a ransomware attack in 2023. This is a serious problem and it is escalating quickly. The most exploitable holes in network security are often older versions of software that are no longer supported or that are supported but have not had the latest patches applied to them.
If you are in a jurisdiction which protects personal information – for instance, the EU or a growing number of States and Provinces in the US and Canada – the theft and release of information contained on yours or your customer’s networks brings additional risks and liabilities.
Your access control system is the first line of security to ensure that only authorised people have access to your building. If the system is hit by a ransomware attack, the results can be catastrophic for your business. Costs to recover data typically are in the tens to hundreds of thousands of dollars.
As integration partners for your customers, there is the risk of being the subject of litigation depending upon who installed and who has responsibility for the servers and whether sufficient steps were taken to ensure that it was protected. The best option for ensuring mission critical data is available is to ensure that offsite copies in well secured servers are available. In short, exactly what is provided by cloud architecture.
In addition to ransomware, general hardware failure, human error and natural disasters introduce potential threats to maintaining a systems’ data integrity. By moving your access control solution to the cloud, you no longer have to worry about servers and dedicated computers. Without a cloud solution, should an incident occur you may need to replace the server and rebuild your system completely. This introduces additional costs and resources better spent on growing a business.
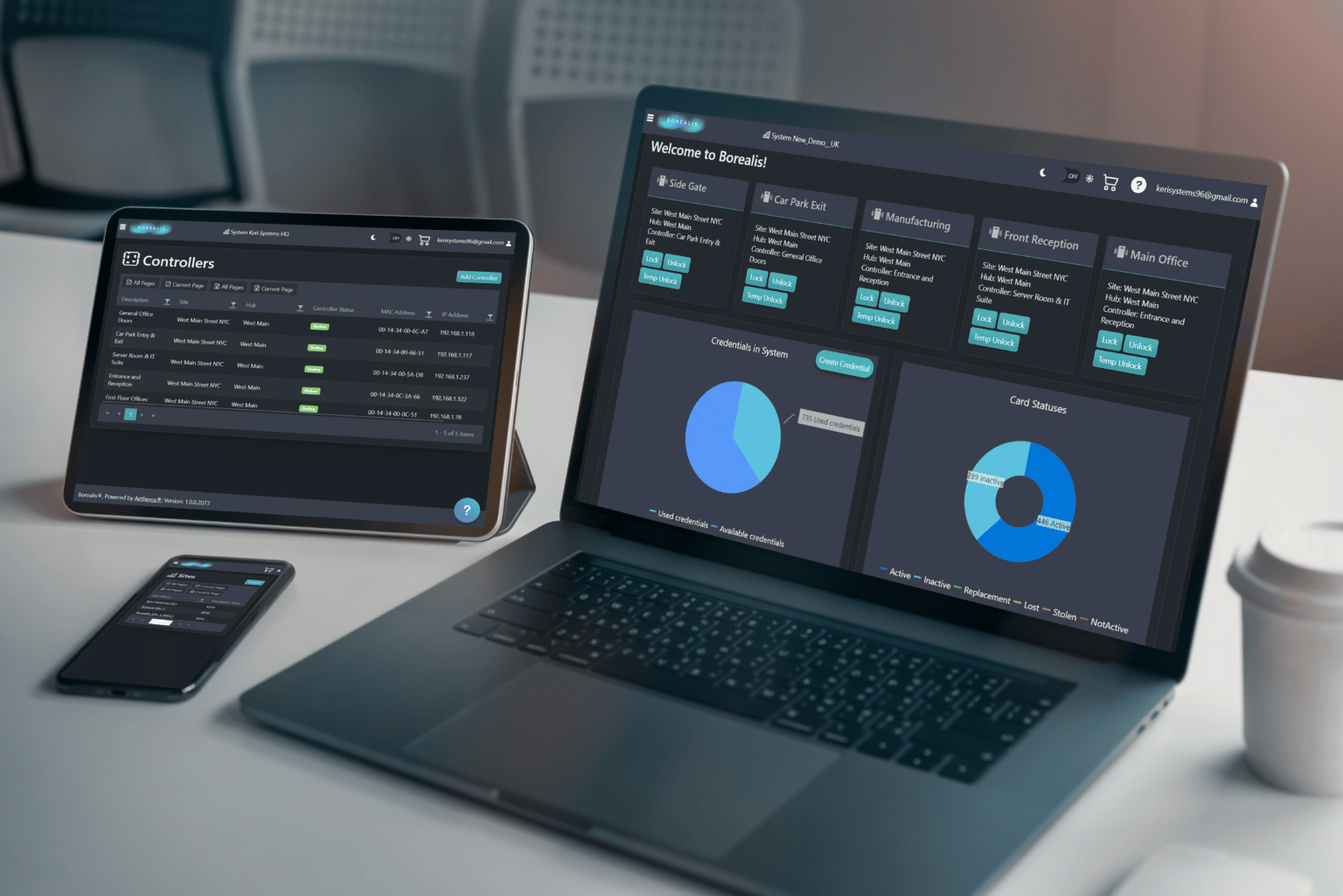
What is Borealis?
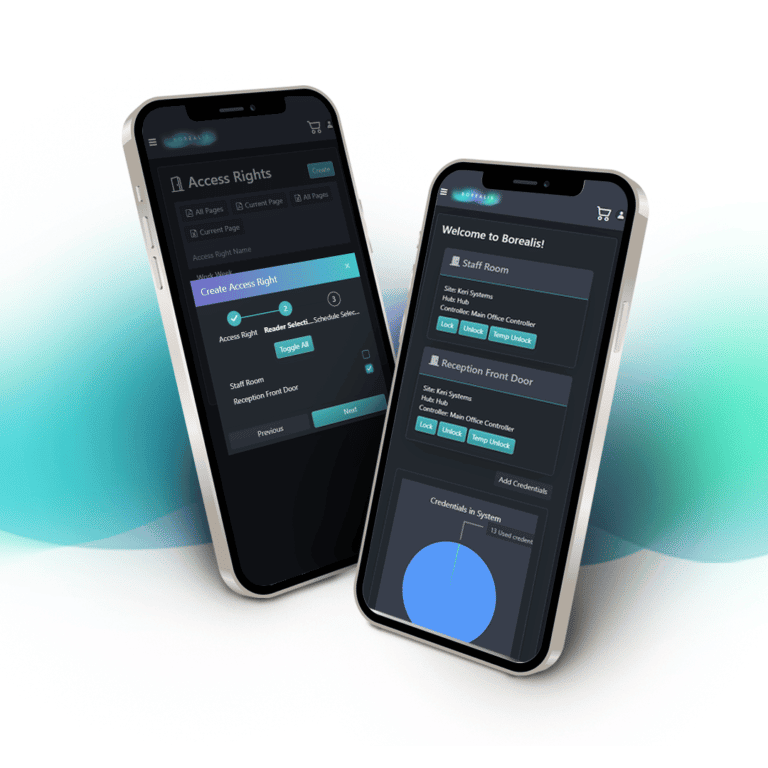
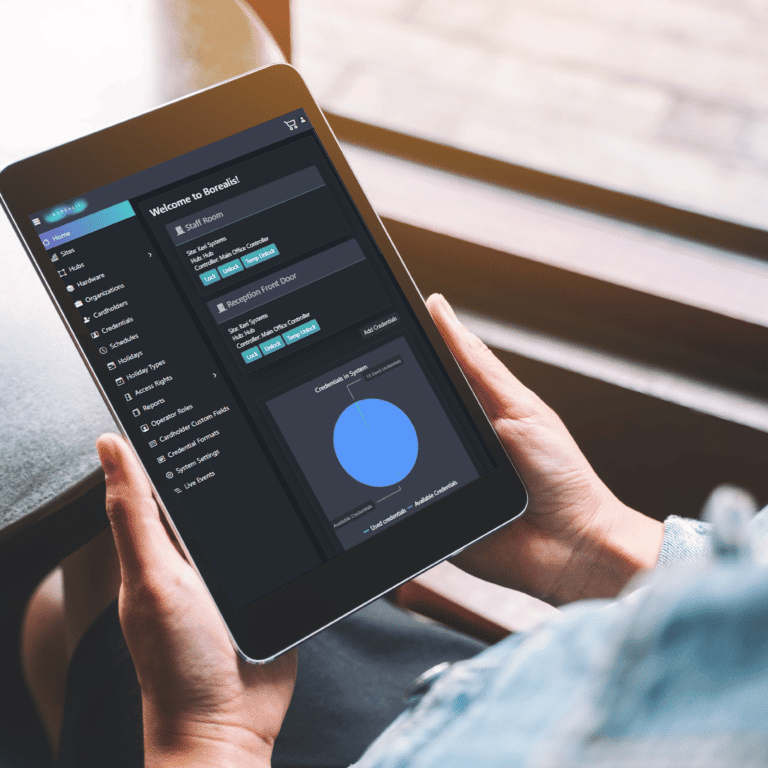
Borealis is Keri System’s cloud access control platform. Developed and hosted on, it utilises the latest tools to ensure security, speed and data integrity. Applications like Borealis boast 99.99% ‘up’ uptime due to AWS’s redundant server architecture and world class security. This means that your data is always secure and readily available when you need it without the need for backups or software updates. It is accessed by any of the common browsers so it provides accessibility from PC’s, tablets or mobiles. Because it is hosted on the cloud and doesn’t require local servers, Borealis scales from one door to tens of thousands with no need to upgrade expensive onsite servers.
Advantages for integrators
Borealis is compatible with Keri NXT family hardware, with support for our legacy PXL controllers and real Mercury hardware coming very soon. This enables you to offer dynamic cloud solutions without learning any new hardware. New features can be added without any additional installation or downtime due to the nature of a cloud solution. Not only can you make changes or view events in an emergency without being physically present, automatic updates mean you always have the latest version of your software. By moving your customer’s access control solutions to the cloud, you no longer have to worry about keeping dedicated computers or servers up to date.
Perhaps the biggest advantage for integrators is the ability to remotely manage you and your customer’s installations. The advantage of remotely logging into any site you manage is that you can perform system diagnostics and even reset hardware; this minimises the need to “roll trucks” to sites, saving time and money and allowing integrator staff to continue to install and service new jobs – a key advantage given the ongoing labour shortages in many regions.
Providing a new path
Borealis was designed to be “Easy to Quote – Easy to Install – Easy to Use” for new jobs. But, Keri has also provided a path for easy upgrades of existing systems, allowing integrators to transition to systems that are easier to support and generate enhanced recurring revenue. However, given the shortfall of labour available to most integrators, Keri has gone one step further and has introduced a full service, “White Glove” conversion program as an option for the company’s Integration Partners.
The process is simple. If you and your customer decide to make the move to Borealis, simply create your integrator organisation within the Borealis portal which acts as your gateway for managing your customers. From there, you can introduce us to your customer contact and Keri will take care of the rest, including converting the data, uploading it to Borealis and pointing the hardware to the new Borealis installation.
This is only the beginning
Borealis has been designed from the ground up using the latest web developer tools and our new cloud architecture allows Borealis to evolve more quickly than ever before. It is one of the most technologically advanced cloud solutions available, with an expansive roadmap of new features, integrations and functionality already scheduled for release.
There is also an open API that makes partner integrations easy going forward. In early Q1 2023, look for releases containing support for Keri’s PXL-500, Authentic Mercury Security products and custom linkages.
Contact Keri Systems to schedule a demo on how Borealis can make your organisation more efficient, enhance your recurring revenue stream and reduce support time. To find out more information, visit: https://kerisys.com/borealis-demo/
This article was originally published in the December 2022 Influencers Edition of International Security Journal. To read your FREE digital edition, click here.



